The vulnerabilities were discovered by Nicolai Grødum of Cisco.
Today, Talos is releasing details of vulnerabilities discovered in Microsoft Edge browser as well as older versions of Google Chrome (CVE-2017-5033) and browsers based on the Webkit such as Apple Safari (CVE-2017-2419) . An attacker may be able to exploit the vulnerabilities and bypass the Content Security Policy set by the server which may lead to disclosure of confidential information. Microsoft stated that this is by design and has declined to patch this issue.
One of the fundamental security mechanisms of a web application is the so called same-origin policy, prescribing which resources may be accessed by the application code. The essence of the same-origin policy is that it allows programmatic access to web resources only to the code that originates from the same server as the data that is being accessed.
For example, a script, executing within the context of a web browser, originating from the server good.example.com should be able to access data from the same server. On the other hand, a script originating from the server evil.example.com should not be able to access any data on good.example.com.
However, many vulnerabilities in web applications allowing the attacker to bypass the same-origin policy have been discovered. One particularly successful attack technique is Cross Site Scripting (XSS). XSS allows the attacker to inject remote code within the context of the original server code executing in the browser. To the browser, the injected code would appear to originate from the same server as the legitimate application therefore allowing access to local resources that can lead to the leak of potentially confidential data to the attacker or even application session hijacking.
Content Security Policy (CSP) is a mechanism designed to prevent XSS attacks by whitelisting servers that may be used as legitimate sources for the client side web application code. Cisco researchers have found a way to bypass the Content Security Policy and allow attackers to exploit the issue and potentially disclose confidential data by injecting otherwise excluded code.
CSP defines the Content-Security-Policy HTTP header that allows creation of a whitelist of sources and instructs the browser to only execute resources from the allowed sources specified by the policy. Even if an attacker finds a way to inject a malicious script and successfully launch a XSS attack by injecting a <script> tag with a remote script source, the remote source will not be matched by the list of allowed sources and will not be executed by the browser.
The Content-Security-Policy HTTP header defines the script-src directive which configures CSP for script code. For example, the line
allows scripts to be loaded only from the server the browser is currently visiting and an additional server good.example.com.
However, an information disclosure vulnerability exists within Microsoft Edge (not patched as of version 40.15063)), Google Chrome (patched) and Safari (patched). An attacker may be able to bypass the policy specified by the Content-Security-Policy header, causing an information leak.
There are three main components to an exploitation attempt: setting the Content-Security-Policy for the browser with "unsafe-inline" directive to allow for inline script code, then using window.open() to open a blank new window, and finally calling the document.write function to write code into the newly created blank window object in order to bypass CSP restrictions put on the document.
The issue, affecting the Microsoft Edge browser as well as older versions of Google Chrome and Firefox is that about:blank page has the same origin as its loading document, but with the CSP restrictions removed which allows for a successful exploitation.
More information about these vulnerabilities is available in the TALOS vulnerability report TALOS-2017-0306.
Information disclosure vulnerabilities may not be as serious as the vulnerabilities allowing the attacker to launch remote code and escape the browser sandbox to access and control the system under attack.
However, XSS attacks that may allow an attacker to exfiltrate confidential data and even take over a user account are considered a serious issue. Content Security Policy is specifically designed with XSS attack prevention in mind and allows the server to whitelist trusted resources that are trusted to be safely executed by a web browser.
Many developers rely on CSP to protect them from XSS and other information disclosure attacks and trust browsers to support the standard. However, it seems that the implementation of CSP within different web browsers differs, allowing attackers to write browser specific code to bypass the content security policy defining the source of the allowed code.
Users are recommended to use browsers with more complete support for the Content security policy mechanism as well as browsers that keep up to date with all newly discovered security vulnerabilities, including information disclosure vulnerabilities such as the ones described in this post.
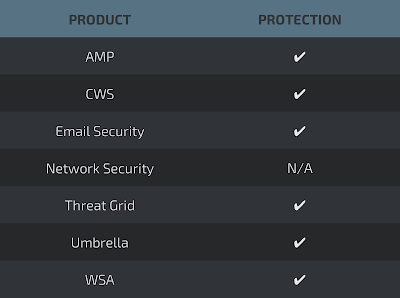
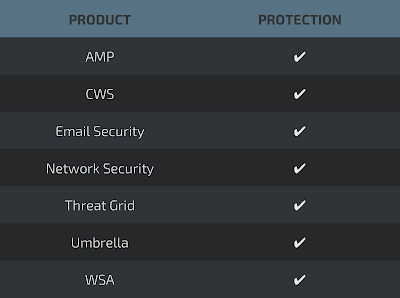
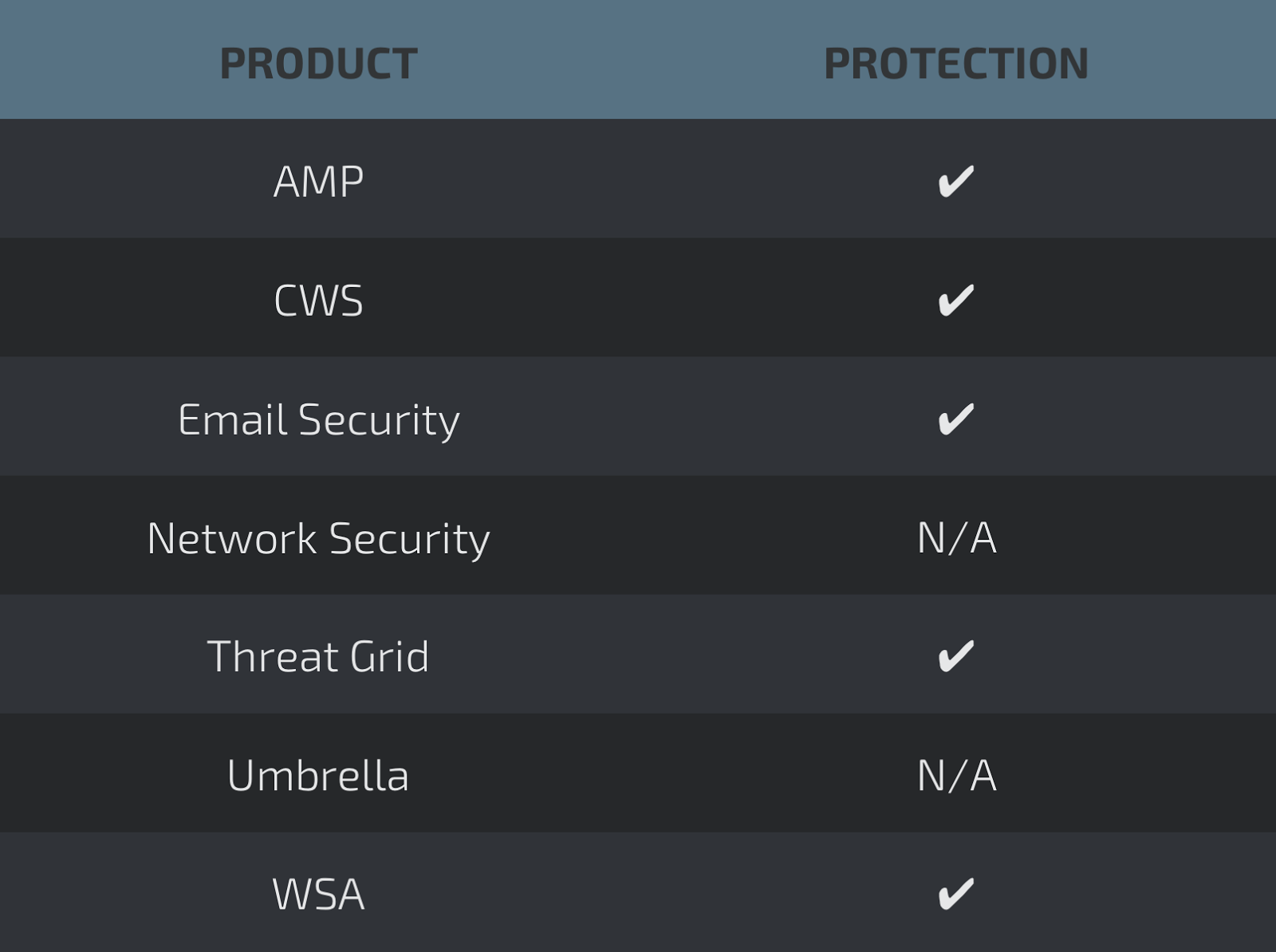
Microsoft Edge (not patched as of version 40.15063)
Google Chrome prior to version 57.0.2987.98 - (CVE-2017-5033)
iOS prior to version 10.3 - (CVE-2017-2419)
Apple Safari prior to version 10.1 - (CVE-2017-2419)
The following Snort Rules will detect exploitation attempts. Note that additional rules may be released at a future date and current rules are subject to change pending additional vulnerability information. For the most current rule information, please refer to your FireSIGHT Management Center or Snort.org.
Snort Rule: 42112
![]()
Today, Talos is releasing details of vulnerabilities discovered in Microsoft Edge browser as well as older versions of Google Chrome (CVE-2017-5033) and browsers based on the Webkit such as Apple Safari (CVE-2017-2419) . An attacker may be able to exploit the vulnerabilities and bypass the Content Security Policy set by the server which may lead to disclosure of confidential information. Microsoft stated that this is by design and has declined to patch this issue.
Overview
For example, a script, executing within the context of a web browser, originating from the server good.example.com should be able to access data from the same server. On the other hand, a script originating from the server evil.example.com should not be able to access any data on good.example.com.
However, many vulnerabilities in web applications allowing the attacker to bypass the same-origin policy have been discovered. One particularly successful attack technique is Cross Site Scripting (XSS). XSS allows the attacker to inject remote code within the context of the original server code executing in the browser. To the browser, the injected code would appear to originate from the same server as the legitimate application therefore allowing access to local resources that can lead to the leak of potentially confidential data to the attacker or even application session hijacking.
Content Security Policy (CSP) is a mechanism designed to prevent XSS attacks by whitelisting servers that may be used as legitimate sources for the client side web application code. Cisco researchers have found a way to bypass the Content Security Policy and allow attackers to exploit the issue and potentially disclose confidential data by injecting otherwise excluded code.
Technical details - Talos-2017-0306 (CVE-2017-2419, CVE-2017-5033)
CSP defines the Content-Security-Policy HTTP header that allows creation of a whitelist of sources and instructs the browser to only execute resources from the allowed sources specified by the policy. Even if an attacker finds a way to inject a malicious script and successfully launch a XSS attack by injecting a <script> tag with a remote script source, the remote source will not be matched by the list of allowed sources and will not be executed by the browser.
The Content-Security-Policy HTTP header defines the script-src directive which configures CSP for script code. For example, the line
Content-Security-Policy: script-src 'self' https://good.example.comallows scripts to be loaded only from the server the browser is currently visiting and an additional server good.example.com.
However, an information disclosure vulnerability exists within Microsoft Edge (not patched as of version 40.15063)), Google Chrome (patched) and Safari (patched). An attacker may be able to bypass the policy specified by the Content-Security-Policy header, causing an information leak.
There are three main components to an exploitation attempt: setting the Content-Security-Policy for the browser with "unsafe-inline" directive to allow for inline script code, then using window.open() to open a blank new window, and finally calling the document.write function to write code into the newly created blank window object in order to bypass CSP restrictions put on the document.
The issue, affecting the Microsoft Edge browser as well as older versions of Google Chrome and Firefox is that about:blank page has the same origin as its loading document, but with the CSP restrictions removed which allows for a successful exploitation.
More information about these vulnerabilities is available in the TALOS vulnerability report TALOS-2017-0306.
Discussion
However, XSS attacks that may allow an attacker to exfiltrate confidential data and even take over a user account are considered a serious issue. Content Security Policy is specifically designed with XSS attack prevention in mind and allows the server to whitelist trusted resources that are trusted to be safely executed by a web browser.
Many developers rely on CSP to protect them from XSS and other information disclosure attacks and trust browsers to support the standard. However, it seems that the implementation of CSP within different web browsers differs, allowing attackers to write browser specific code to bypass the content security policy defining the source of the allowed code.
Users are recommended to use browsers with more complete support for the Content security policy mechanism as well as browsers that keep up to date with all newly discovered security vulnerabilities, including information disclosure vulnerabilities such as the ones described in this post.
Affected versions
Google Chrome prior to version 57.0.2987.98 - (CVE-2017-5033)
iOS prior to version 10.3 - (CVE-2017-2419)
Apple Safari prior to version 10.1 - (CVE-2017-2419)
Coverage
Snort Rule: 42112