Today, Talos is publishing a glimpse into the most prevalent threats we've observed between April 7 and April 14. As with previous round-ups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavior characteristics, indicators of compromise, and how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of date of publication. Detection and coverage for the following threats is subject to updates pending additional threat or vulnerability analysis. For the most current information, please refer to your FireSIGHT Management Center, Snort.org, or ClamAV.net.
This week's most prevalent threats are:
File Hashes
ThreatGrid
Registry Keys
Please note this is an non-exhaustive list.
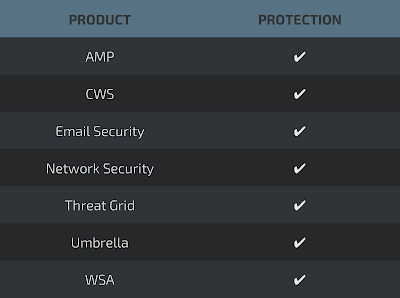
AMP
ThreatGrid
Umbrella
ThreatGrid
File Hashes
Please note this list is not exhaustive.
AMP
ThreatGrid
Umbrella
Malware Screenshot
Registry Keys
ThreatGrid
ThreatGrid
Malware Screenshot
ThreatGrid
Umbrella
Malware Screenshots
ThreatGrid
Umbrella
Screenshot
Registry Keys
![]()
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of date of publication. Detection and coverage for the following threats is subject to updates pending additional threat or vulnerability analysis. For the most current information, please refer to your FireSIGHT Management Center, Snort.org, or ClamAV.net.
This week's most prevalent threats are:
- Java.Trojan.Adwind-6260775-0
Remote Access Trojan
Also named AlienSpy, Frutas, JRat… Adwind is a java based Remote Access Trojan that is usually distributed by email. Given it is Java based, it is portable across different operating systems and even mobile devices. It allows to capture keystrokes, record video and audio, steal cached password and stored data, etc...
- Win.Trojan.VBSinkDropper
Dropper
This sample is written in Visual Basic and its main goal is to drop and execute a second stage payload. The domains are related to the Zeus trojan, indicating this is probably a Zeus variant. The sample is heavily obfuscated and has anti-debugging and anti-VM techniques to hinder the analysis and performs code injection in other processes address spaces. This sample is currently delivered in massive spam campaigns as an attachment.
- Win.Trojan.AutoIt-6260345-0
Trojan-Dropper
The initial binary contains an AutoIt script. The script is obfuscated. It creates several in-memory DLL structures with AutoIt’s DllStructCreate and DllStructSetData. The script then executes the shell code injected into these DLL structures.
- Win.Ransomware.Cerber-6267996-1
Ransomware family
Cerber is a popular ransomware family that continues to undergo active development to continue being dropped in the wild. It still drops multiple ransom notes, including a desktop wallpaper as a warning post.
- Win.Virus.Hematite-6232506-0
File Infector
Hematite is a simple but effective virus that spreads through executables. It scans the victim’s machine for any files with the extension .exe. Hematite appends 3000 bytes of malicious shellcode to the end of each file, then modifies the entrypoint of the original executable to load and execute the shellcode.
- Doc.Dropper.Agent-6249585-0
Office VBA/PowerShell downloader/dropper
This sample is a Microsoft Word document that uses a macro to launch a PowerShell script to download and execute a secondary payload.
- Win.Virus.Sality-6193004-1
Windows file infector
Sality is a file infector that establishes a peer-to-peer botnet. Although it’s been prevalent for over a decade, we continue to see new samples that require marginal attention in order to remain consistent with detection. Once perimeter security has been bypassed by a Sality client, the end goal is to execute a downloader component capable of executing additional malware.
- Doc.Dropper.Dridex-6260340-0
Office Macro-based Downloader
Dridex documents leverage Microsoft Office to deliver a malware payload. They have been used often with banking trojans and ransomware such as CryptXXX and Locky. This week Doc.Dropper.Dridex-6260340-0 has been delivering Cerber as redchip2.exe.
- Doc.Macro.CmdC-6249572-0
Office Macro Obfuscation Heuristic
Office macro code is used to further compromise a target system. This heuristics focuses on macro techniques to obfuscate shell commands that will be executed to further compromise the system.
- Js.File.MaliciousHeuristic-6260279-2
JavaScript Obfuscation Heuristic
To make javascript harder to signature on, detect or to manually analyze; obfuscation is applied by breaking up functionality into small function.
Threats
Java.Trojan.Adwind-6260775-0
Indicators of Compromise
Registry Keys- MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\[application name].exe
- Value: MAXIMUM ALLOWED
- USER\[uuid]\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: [a-zA-Z]+
- Data: "C:\Users\[user]\AppData\Roaming\Oracle\bin\javaw.exe" -jar "C:\Users\[user]\[a-zA-Z]+\[a-zA-Z]+.[a-zA-Z]+"
- USER\[uuid]\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\ASSOCIATIONS
- Value: LowRiskFileTypes
Data: .avi;.bat;.com;.cmd;.exe;.htm;.html;.lnk;.mpg;.mpeg;.mov;.mp3;.msi;.m3u;.rar;.reg;.txt;.vbs;.wav;.zip;.jar; - MACHINE\SOFTWARE\POLICIES\MICROSOFT\WINDOWS NT\SYSTEMRESTORE
- Value: DisableConfig
Data: 1 - MACHINE\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
- Value: EnableLUA
Data: 0
- N/A
- 174.127.99[.]134:2888
- N/A
- \Users\[user]\AppData\Local\Temp\Retrive[0-9]+.vbs
- Kills AV solutions / security tools
- taskkill.exe taskkill /IM K7AVScan.exe /T /F
- taskkill.exe taskkill /IM V3Proxy.exe /T /F
- taskkill.exe taskkill /IM mbam.exe /T /F
- taskkill.exe taskkill /IM text2pcap.exe /T /F
- taskkill.exe taskkill /IM FPWin.exe /T /F
- taskkill.exe taskkill /IM FSM32.EXE /T /F
- taskkill.exe taskkill /IM cmdagent.exe /T /F
- taskkill.exe taskkill /IM ClamWin.exe /T /F
- taskkill.exe taskkill /IM MpCmdRun.exe /T /F
- taskkill.exe taskkill /IM V3Svc.exe /T /F
- taskkill.exe taskkill /IM GdBgInx64.exe /T /F
- taskkill.exe taskkill /IM freshclamwrap.exe /T /F
- taskkill.exe taskkill /IM rawshark.exe /T /F
- taskkill.exe taskkill /IM MsMpEng.exe /T /F
- taskkill.exe taskkill /IM PSANHost.exe /T /F
- taskkill.exe taskkill /IM NisSrv.exe /T /F
- taskkill.exe taskkill /IM BullGuardUpdate.exe /T /F
- taskkill.exe taskkill /IM procexp.exe /T /F
- taskkill.exe taskkill /IM nfservice.exe /T /F
- taskkill.exe taskkill /IM VIEWTCP.EXE /T /F
- taskkill.exe taskkill /IM K7TSecurity.exe /T /F
- taskkill.exe taskkill /IM UserAccountControlSettings.exe /T /F
- taskkill.exe taskkill /IM QUHLPSVC.EXE /T /F
- taskkill.exe taskkill /IM V3Up.exe /T /F
- taskkill.exe taskkill /IM CONSCTLX.EXE /T /F
- taskkill.exe taskkill /IM K7AVScan.exe /T /F
- taskkill.exe taskkill /IM MWASER.EXE /T /F
- taskkill.exe taskkill /IM K7CrvSvc.exe /T /F
- taskkill.exe taskkill /IM editcap.exe /T /F
- taskkill.exe taskkill /IM LittleHook.exe /T /F
- taskkill.exe taskkill /IM ProcessHacker.exe /T /F
- taskkill.exe taskkill /IM cis.exe /T /F
- taskkill.exe taskkill /IM MSASCui.exe /T /F
- taskkill.exe taskkill /IM SSUpdate64.exe /T /F
- taskkill.exe taskkill /IM mergecap.exe /T /F
- taskkill.exe taskkill /IM FSHDLL64.exe /T /F
- taskkill.exe taskkill /IM AdAwareTray.exe /T /F
- taskkill.exe taskkill /IM guardxkickoff_x64.exe /T /F
- taskkill.exe taskkill /IM econceal.exe /T /F
- Hides files in the filesystem
- attrib.exe attrib +h "C:\Users\[user]\[a-zA-Z]+\*.*"
File Hashes
- e084341b5149d62ebd26f311e51725d3e630f5d1c154568b717d79aa0b72c441
Coverage
Screenshots of Detection
AMPThreatGrid
Win.Trojan.VBSinkDropper
Indicators of Compromise
Registry Keys
- HKEY_USERS\Software\Microsoft\[a-z]{5}
- HKEY_USERS\Software\Microsoft\Windows\ShellNoRoam\MUICache
- HKEY_USERS\Software\Microsoft\Visual Basic
- N/A
- 191.96.15[.]154
- 154.66.197[.]59
- 191.101.243[.]203
- 108.170.51[.]58
- afrirent[.]net
- ogb.mmosolicllp[.]sk
- norlcangroup[.]com
- C:\Documents and Settings\Administrator\Application Data\Xoabhaul\[a-z]{8}.exe
- C:\Documents and Settings\Administrator\Local Settings\Temp\subfolder\[a-z]{3}.exe
- C:\Documents and Settings\Administrator\Local Settings\Temp\Purchase Order.doc
Please note this is an non-exhaustive list.
- 00062f3d06aad63d025c8097e0bc024f23ede453751afdae0e1cc5b40f987bf6
- 0094bcc3a70b00b2b61701a90ac2c15f3d39551adcf18b33cafb6ad8a732825c
- 029a6ba06418d2cc2ee9e7dbbcca622b206df8a1855fa6e551c6126f07302030
- 03580fcc6fa4d72a39b876067ae9a7c9b9c62b1a53175df0f54a2a47deee6691
Coverage
Screenshots of Detection
AMP
ThreatGrid
Umbrella
Win.Trojan.AutoIt-6260345-0
Indicators of Compromise
Registry Keys- N/A
- N/A
- N/A
- N/A
- The malware copies itself to %AppData%\driver--grap.exe
- e6ea4d5f3bc4b53ec4777f5da3105d75cd53dd6ed4f0497b52f09f79e7183891
- 7d05f85efe8f289d43cc3515c2399e2c8d1bfbf082fddaebaf3c9c6dcea6381d
- 5eafd63e278510033918f63f34dae687f7a19d1fc04b479ebc09c507037409ef
- 5fdb796f505f40a0a9add787776f12ddb02edd310ae24c9d4bd5d149fa0602c8
- 65f372559761f703622fbe2d433f5bb92752d3cb5e17966ef987c5b40a03010d
- 9c4be24f3245e733890ac12c8a9e2fe2a0e3be31df16edf86354cd80eccc3e95
- a204c517252f0fb7994d4472bf0090182054825822a9d29ecb370df7c8f0d3ba
- f7667ff6110302df2855156ad8f93e998ce646109568d443a4aac514cab71edf
- 9b816ef40eb06982b227beaf91c2eb9bc352c915632638972f3af1c3cbb29fa5
- 5d3324155753948adf84a3f8f0c9d69dc272929d66e294faf54689e4537c15f6
- 0fa2383f17d23286efee1062322964550636add6d2ceba1abbeb87aead6c1649
- d69224eeda882e34339f5f785181f49e074c3f07444d8daeaf27dfddea19cee6
- 503ac78c383a62d207512e361af07e7be279d64237c456eb376825485a1f5dc3
- 25bf3a2df95236cce230163e9929dab6b01242be6364c6b3de186cff8e8883df
- dadc2e7ea2fb8cb732a3baae2d0b2978d0ee9398d8e8c12f20a2e3ede7752045
- 6157a7293e25ab26fa360f11f1b84abe44f62f363fc284af2a2787cfb6aa4a0e
- 7616cdc6a6619685e5a6a1534264a988f14add3192bd3fb467dce54234635026
- 613770d0d5a1f8d8bfa39cb52bd2c4357aba183afd9ecc5c3c238e5a0aea3d8e
- f8d0bac2dfc3dd7e16905497b427391f7887effe1ae3e3276411d5c13c416ca1
- fd55686aab2686c4af73dbac6959cbf26e4c24fb83953d7495cc680d48d73754
Coverage
Screenshots of Detection
AMPThreatGrid
Win.Ransomware.Cerber-6267996-1
Indicators of Compromise
Registry Keys- N/A
- N/A
- N/A
- api[.]blockcypher[.]com
- hjhqmbxyinislkkt[.]1efxa8[.]top
- %USERPROFILE%\Desktop\_HELP_HELP_HELP_[A-Z0-9]{4,7}_.png
- %USERPROFILE%\Desktop\_HELP_HELP_HELP_[A-Z0-9]{4,7}_.hta
- %SystemDrive%\_HELP_HELP_HELP_[A-Z0-9]{4,7}_.png
- %SystemDrive%\_HELP_HELP_HELP_[A-Z0-9]{4,7}_.hta
File Hashes
Please note this list is not exhaustive.
- 04abd9e0fe7d1ea53836de6429bdca8f2db992e203675e0dc36b75355fd0432d
- 0b9cbc73f23208828a6c92fc85cadf31e22fe0b8852a100f72418394de455854
- 6f93a071e1b7f33f62cb0ebdade39826d1fb2539dfe3d3bb5329f1b05f01d2d1
- 37e6f3b2a5228e10564bafcec2ca700359d5e9265d6f6d1c57a275007760876b
- 01eb9e772dcae43eb4c8d23c69775dfe18ec133b2650663a81f40861728dac4c
- 09e6190ac04db46f1463c539a80973d9de17de23fc11a87adcc59a78950df342
- 648f4e50848a55deb1c51fa8d82674bc7dbf3c630c6b6956c015258157736389
- 07514ea42b4da1110166369fd3ed806189f3c3731717e51dfb5f2835a0fbf6bc
- 635007aedf337778cc75d4dc51e25041b89faa06c91a40378d86224dd1230e36
- 4cf1591e9e49d796183ce7a55420cd54681afbe1ebfe6e012cceb35f74c75dbb
Coverage
Screenshots of Detection
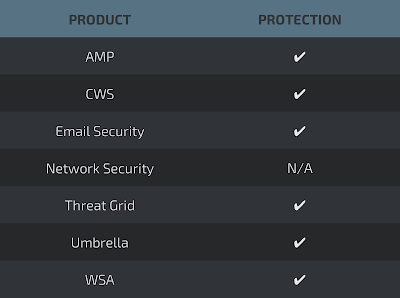
AMP
ThreatGrid
Umbrella
Malware Screenshot
Win.Virus.Hematite-6232506-0
Indicators of Compromise
Registry Keys
- N/A
- N/A
- N/A
- N/A
- N/A
- N/A
Coverage
Screenshots of Detection
AMPThreatGrid
Doc.Dropper.Agent-6249585-0
Indicators of Compromise
IP Addresses- 217.23.12[.]111
- N/A
- %TEMP%\uuqjd.exe
- 79fb46efcdff1f2e5ab8114f2e4d27de56d72ef2b01664870108793663b1c85e
- 1007936720cdcb884a675912ee552d13d7e2a9c77fdcb7602380f5b789c55354
- 79fb46efcdff1f2e5ab8114f2e4d27de56d72ef2b01664870108793663b1c85e
- 89847e43aec98d5f80488b6ed609dfc50fab8df248267ae9bd57de4d5fa4815e
- ebd2775940368bcbd9717bac69f68fa53012013bf4091d2a8506df1cf82a7ce4
Coverage
Screenshots of Detection
AMPThreatGrid
Malware Screenshot
Win.Virus.Sality-6193004-1
Indicators of Compromise
Registry Keys- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\Svc
- HKEY_USERS\Software\Fobvexllmtqkq
- HKEY_USERS\Software\Fobvexllmtqkq\-993627007
- \BaseNamedObjects\xx19867861872901047sdf
- \BaseNamedObjects\winbmcavr.exeM_584_
- \BaseNamedObjects\uxJLpe1m
- 94.76.225[.]131
- N/A
- %SystemRoot%\ab4f7
- %TEMP%\winksbq.exe
- %SystemRoot%\rugrijfnvpkmu.log
- %SystemRoot%\system32\drivers\sfmom.sys
- %SystemDrive%\kojchn.exe
- cf3eda07e7394abcd11b9d63e9489c8c5ef9d799d79f111e78aefeed44136475
Coverage
Screenshots of Detection
AMPThreatGrid
Doc.Dropper.Dridex-6260340-0
Indicators of Compromise
IP Addresses- 104.41.146[.]46
- 13.65.245[.]138
- 13.65.245[.]138
- 131.107.255[.]255
- 134.184.129[.]2
- 138.201.223[.]6
- 143.95.251[.]11
- 184.169.138[.]0
- 185.20.29[.]90
- 185.75.47[.]96
- 185.82.217[.]110
- 192.254.183[.]111
- 208.113.184[.]69
- 208.115.216[.]66
- 212.19.96[.]44
- 213.98.59[.]242
- 27.254.36[.]68
- 37.152.88[.]54
- 40.84.199[.]233
- 52.178.167[.]109
- 59.188.5[.]122
- 64.111.126[.]184
- 72.13.63[.]55
- 72.52.4[.]119
- 74.209.240[.]161
- 82.208.10[.]231
- 85.114.146[.]10
- 91.121.36[.]222
- 91.215.152[.]210
- 93.184.216[.]34
- 94.23.19[.]56
- abcdef[.]hr
- animo[.]br
- dva[.]hr
- ektro[.]cz
- emaiserver[.]ro
- fafa[.]pk
- fb[.]cz
- libertynet[.]org
- litwareinc[.]com
- musical.com[.]br
- negdje[.]hr
- orice[.]com
- philteksystem[.]com
- pirajui[.]br
- poveglianoatuttogas[.]org
- ppp[.]ro
- princehkg[.]com
- proseware[.]com
- quatro[.]br
- rockgarden.co[.]th
- tek-astore[.]cz
- villa-kunterbunt-geseke[.]de
- vlada[.]hr
- vub.ac[.]be
- www.offertevacanzeshock[.]net
- www.philteksystem[.]com
- www.soulcube[.]com
- xara[.]pl
- xyz.com[.]br
- redchip2.exe
- 01b12a002debc9820f93b6a9086412c19e1f6d9668673cc2cc1f6c93aabfd8d6
- 049bc0d32a6b918ca4fd65cb183bcb2c0ff06628d4fc6c42ae092d0ab0be7604
- 0c7f7dfc2b6945f46b96c8c62aa0fd9f9694fe9645ce6be52d85788ff687e76e
- 0cfdb3ef99de18a48291ad6a900026b788e40045cf2ab84f84297a1a5df06623
- 0d493c55eb56321b022dcac836ea01e5b0ea29610bc8690baa979e14580d50b1
- 1084f2ecde7fb1be955cf465854439843e9a4e8ac8ff85232b6d1bf1fff4839b
- 15063800322f6fa377dcc9b21a7283174922ab37cb84e519cd838fc76bb70eb9
- 1678fe4b970b78989ca8abe3c830f4e110b6bca57de4ac701e7aee3b28dc6360
- 167ed42bfeeed279d6d6633b3e4f449fbc8ddd6afb3c71ecf004d04d8196cd3e
- 176722ee68098d6e3788c61b901976692b506b3ebc4ef750e4358c14ac764e5b
- 17ae9aac1dcea2d5a134393fc8b0a764f5e0c6844a8cea57ec76e34e7ba9d28e
- 1b7210dce366e228d20cbe1ce61d9970f1668a16e5c49a98fd7cda941a424250
- 1bc207f9a7d0934afbd74bd1283ce6479ab11354406428c798432992f88af579
- 1cf1178bb1a391756fab1273c62fec1be4b594ace355da3e71c45c74a92a0870
- 1e5da3edef25c914e15b40f8b3e435eb462acfed2a15167c9a7ad6c9180def05
- 1f490a190ef296c8cd6cd2df5eb4671e02b5c3de39059bd98e4216bca08dedb3
- 24f6690360a0f839b14fdd4620f56f72380b0bf086b130a1921640212d2ab716
- 2647e99046ec808e3aafe5cc1764902888b75acc89d8126545c0d37a56d85dd8
- 28a91316512591938857a4264396f775851a2e7a25f6dff665057ae95e06dd8c
- 28ab7ec22ff42b301c6336b9aaa53bb3aace63675e93eb7907c1680d7936f331
- 2b3f8964155c237e9ff28d505e0756e1873ed9f2e56f04b8dbe6862e188b1a4b
- 2dba0ea599270832f5b88fbe71c7795ba3c36a44ab573a157b615b93c78cf389
- 2e0683cd448ed61994e38789224545963a37d59dbaa49f4f24a3740674d4ec12
- 30924070e951f97dee75990fe0a9651d8a87267e511f6172ca5ec3446dddb02f
- 38898c7d496439e9e5da5e4cc40d65aa5fae348085f2406b66810be14cb7e47e
- 3c35385c0fe82b7f62fe95ba73aa9e4ff8d22a4193d59c11ff262650cb5f27cc
- 3db4d968b4dff8a15379d9f2e0f1084c96d8d480dbf7ad53e7e9e8e47899a727
- 3ff9e1394bd51320bb30280575913d91783a6b9f63f5d4b739851726f0ed8f01
- 402a54cd56f699250064032c71e27a2a981affdf22248cc59a2599c6407d94d5
- 4202e58c98095862c4bcdbd55c98b42788d951879f7f82341dca213a1524ff0a
- 46080bd19531929fa0bef917ed8de88946cd4029eaaaaf9fc593514ff9384e49
- 49119b680f9fedb19b9e1b36046b12d05ebbee4ef1040b33b9e1e4afcd38c3a1
- 493cffa37b28beee9e404b48ab82953a61fe1bdfa41b68ea34336b817eec6438
- 4d1960e5b18624f8ffe659719a6af49806a661abc4776fb9da173907105a0016
- 4f13124b24c71e2d8c551f9d5123aecd49b5632cedc93d0b8a8ebc4adf244270
- 5262369be5e983a682c9bb59fbbef0fc3dfc98feaf85278a319fb026fec93cd1
- 55bb1ea2b1504d28fc397543e55f3c301fb58803d4e8448a38f53ba29d24bc9a
- 57bf408c7525458ed58ae59dc57a7d0574cb6b453ab2e3e735ab93a94db61471
- 584c8bfbf964695949fcd0c8a66e0beb1d4803afe4977e504c721a7ce38e97a0
- 58c52566376771654ec4bd135c92ee7fe03795b1dc4f81e0609f4252f803e889
- 14230d3e19cbef146e83bc7e6bed4f08eb8857a8a11765a09dece6458cf998d5 (redchip2.exe (Cerber))
Coverage
Screenshots of Detection
AMPUmbrella
Malware Screenshots
Doc.Macro.CmdC-6249572-0
Indicators of Compromise
Registry Keys- N/A
- N/A
- N/A
- gosterd[.]pl
- ywkl.nonfect[.]com
- etesusozim.nonfect[.]com
- urojab.nonfect[.]com
- abap.nonfect[.]com
- knygobynuwa.nonfect[.]com
- ohpkyxij.nonfect[.]com
- ofinepi.nonfect[.]com
- asode.nonfect[.]com
- otos.nonfect[.]com
- egaqf.nonfect[.]com
- djirus.nonfect[.]com
- olyfabe.nonfect[.]com
- yloked.nonfect[.]com
- ydgnucif.nonfect[.]com
- ygudu.nonfect[.]com
- ovislragil.nonfect[.]com
- onem.nonfect[.]com
- ybelikyvygo.nonfect[.]com
- ijezqqwgamy.nonfect[.]com
- ytijaboqo.nonfect[.]com
- ogazedy.nonfect[.]com
- ucigudago.nonfect[.]com
- omisagirul.nonfect[.]com
- %WINDIR%\hh.exe
- %ALLUSERSPROFILE%\<random_folder_name>\<random_file_name>
- 8f314f6773f6ef4af43432c49756c9a4af32b2fe0e0ca91937972728421ea1b6
- 318cb81cf8ee609f8a6a8e8866bf4bc48013c6cf75ecfb1d806c523afbd3589b
- a5f0aaa5e33615ab666d92b3542792d2be582bf6b0e8f3c0d2bee86ecbe552d4
- 741d5e7d7cc13a496440c26b1bbe0080307338e9e419a154470855a5b1157ba3
- 85d1f6ad4c4babe1a5bbde3d583411142e6cefa60631f8a5f3f7b823a107b51e
- 99f8c220519c82de58ddf609cd5de57b6542addea00213e068030d2c5d9d6763
- 00abd8fb0560766aef3dd884677a643244e56b03c3a4b82dea6d79d7d2f04a29
- e12e25b9871268adb4540ed866f47d653632d85fcdcc737ddf69e99e1bc9782c
- 61d68dbbed963678323be37753159f381e0c21e8c56fc8cbd1acd3ea5c669e12
- 64d03eaa413a3efae12a4f72967b64625afaa0f01caf69349377795683a0c79f
- 76a0bfa693a9d7c312c36050ff497aaa0d423a6f335ff204d4c8334d3cc8be8f
- 253f451f36a49e093191e5583cf4a3041407082168b29299429e66d968a186ba
- c0982749d0bef7b337f4f737f683a6ba63794ada050adfec2d094b7e55ad4355
- ea8619a50fbdd60b797880fbd725e6d0e495d23447d365a31076837058b982ce
- 873166cbaa52eb4e24d96097de6f5b3322012f8e4aacdecf380476624e909b6d
- a81534f11ee7875199487f926a96b53af265afb7f96e97bdb0c477d3d18c4614
- e62f33ff3c59c1f4ac633e228a3693e7a9f3eaf0385a41633e24dc4260d683b1
- 215dedd739516fb6054d0b6cfc0863c9f71c56479521362fd0e088536efd4191
- 39ed73fe10a6aa325322399c0038a8e405a27a66cf740c975418021efa5da457
- 3c574a5e6e8994691ee39855b85fba9d961ce807e77b65093fa875292da1d5a7
- 5ac4f7bd73fbf822c5e5e7a319776c1b79593b7604fae84c0598a1d2e99a567a
- 6a24dbe8aeabcaea4bc9454815751037cfd1da4a82359b830df93eb67452809e
- 6f34227aa29d33d4e7b853743818006900bb9df39cf3e6bd86cf7a1836b9a2d9
- a1e1dd4ed46ccb95b2f95ad57a582e7df8422e4c2ebdf853356701b6ad6cc2e2
- b42f91110d802e4363ce9664d5401f84beb08328c8e8d81a50290f49758ba434
Coverage
Screenshots of Detection
AMPThreatGrid
Umbrella
Screenshot
Js.File.MaliciousHeuristic-6260279-2
Indicators of Compromise
Registry Keys
- N/A
- N/A
- N/A
- N/A
- N/A
- 18ec2f58ca800b00e0abc6cb7235a3caa65d120ba1fe14ad8160c3c3f450e19a
- 352540dce31dc80bd938fc90a06322b8fcbb2e1db7a76d254eabc93cca4e9a5e
- 4bb8119527c8da29ce70926efe15fed0305a3b9518da40f9551ee62606f3dccf
- 5a6526a7753245fc0837ea3b8a536fd5e587dafa3aa2fe58e58f69132404639d
- 5fc98c58ee911fad22e27203b649d78ddff67503357038c0c7a2733ebe70d8e0
- 72e173a8c5828a7eb2f6e29ae047492d7d5ed030d8c126c6259a4be147debcbd
- 860302d167ec4aad867b193eebc60fca7bf407f01ef58de6957c1b0ff6f5cd7b
- 914680df0be91b8c175c08ec050d443a60a0b7bfce3bc4136d08d432e0a0d3db
- 91cd175bddcd53bbafccb70356b9bae310cbadaa864494a19f47a46b5523cda3
- 99b9911869b733d6cbfeedcdbd9ae165f8250d1b9cfb62af05e314c62d502548
- a7227042a9d48e78a696ee0e45066a324b3a0b32ec24b35cf96b38550f991e92
- aaa8a4c8afa43f8a0bd5cffb1e1a01dc503d7c9ba4b646789107e12d68f66ab4
- aeffb11a5ede257b91c8f1a481ff7c27f74774cb32665d04cf3a92fc9c7be14e
- dee2a92b982ee9ad225f8ee7a5b393ce78604cd41f094fa058891e09e97f242d
- e3a01bd742364862ea7336574fd030c8e53bfb9819b5458976fe6e7107a120c9
- e3ce60862c0d258511c492a03b3adb5d86c665f490fe231997045a1ddf5b2daf
- e3e4bbd670fe41e6608b0e17778ddf70b2c2e37591b265bc16089f84ee7ef7fb
- ece6551b97bd990b40a78d683943e48313be26a46daeded3b232e4ec47814adf
- f873d1bf619f28ac6200d8d669c3bba5bd69b0cdbd513d6d9461bc6c308e416c
Coverage
Screenshots of Detection
- N/A